This is the text and main graphic from Online Course 2214 MPLS and Carrier Networks Lesson 11: TCP/IP over MPLS.
The interactive animated version is available here and the YouTube version is available here.
NOTE: You may find this tutorial a bit overwhelming, landing smack on your computer screen with no preparation, like a parachutist whose chute didn't open landing in a cow field.
In the Online Course "MPLS and Carrier Networks", there are TEN lessons building up to this one. Actually, two courses: " The OSI Layers and Protocol Stacks" and "IP Networks, Routers and Addresses" are prerequisites... THIRTY-FIVE lessons building up to this one.
So... if you are already familiar with the OSI Layers and protocol stacks, and IP packets and LANs, you'll find the following lesson easier to follow.
If you're not already familiar with those pre-requisites, then you might want to watch some other free tutorials first: Video Tutorial VT-3 "Packets, Frames, Addresses and Routing", Video Tutorial VT-4 OSI Layers: The FedEx Analogy, and the "Datacom and Networking Fundamentals" section of our free online tutorials.
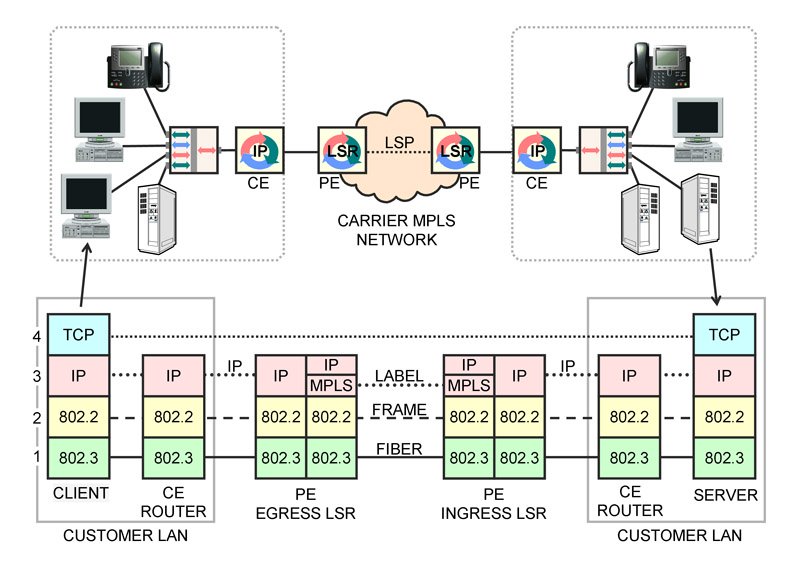
Starting with the server on the right, which is downloading a file to the client on the left, the file transfer software takes a segment of the file and gives it to the TCP software on the server, which starts a timer, puts a sequence number, error check and source and destination application port number in a TCP header on the file segment, and passes this to the IP software on the server.
The IP software on the server creates an IP packet by adding the IP header, populating the source address with its IP address and the destination address with the IP address of the client on the left.
The IP packet is passed to the layer 2 LAN driver software on the server, which puts the packet in an LAN MAC frame, populating the source address with its MAC address and the destination as the MAC address of the right-hand Customer Edge router.
The frame is then signaled one bit at a time over the LAN cable connecting the server to the LAN switch, which directs the frame to the right-hand CE router.
Layer 2 software on that right-hand CE router receives the MAC frame from the sever via the switch, performs the error check, verifies that its MAC address is the destination, then extracts the IP packet and passes it to the IP routing software on the CE router.
The IP routing software on the CE router decides that the Provider Edge router is the next hop, puts the packet in a MAC frame, populates the destination MAC address with that of the PE, recalculates the error check and signals the frame one bit at a time over the Gigabit Ethernet over fiber access circuit to the service provider's Provider Edge, which is the ingress to the carrier's MPLS network.
The Provider Edge is the ingress Label Edge Router. It receives the IP packet in a MAC frame over the fiber access circuit. This ingress device examines the destination IP address on the packet and along with other factors, decides what Forwarding Equivalence Class the packet belongs to, then implements its decision by pushing a label onto the packet.
It then does a table lookup in its Incoming Label Map to get the Next Hop Label Forwarding Entry, determines what LSR that items with this label are forwarded to, and transmits the labelled packet in a frame to that LSR on the appropriate circuit.
Each LSR in the middle of the network (not shown) receives a frame, extracts the packet then only looks at the label and performs a table lookup to determine where to forward the packet and possibly what relative priority it has.
Eventually, the labelled packet is delivered to the PE on the left, the network's egress Label Edge Router. This device pops the label off the packet and removes the MPLS header, then uses conventional IP routing to send the IP packet in an MAC frame over the access circuit to the CE router on the left.
The CE router on the left receives the IP packet in a MAC frame, passes it to its routing software, which must at this point determine which station on the LAN, which MAC address, has been assigned that IP address.
It first looks in its cache, which is a table relating IP addresses to MAC addresses. If it does not find an entry, it broadcasts an address resolution request to all stations on the LAN at the left, asking "who owns this IP address?" The client responds with its MAC address. The premise router saves that information in the cache, then puts the packet in a MAC frame with the client's MAC address as the destination, then signals the frame one bit at a time to the left-hand LAN switch, which directs the frame to the client.
Layer 2 software on the client receives the frame over the LAN cable, extracts the IP packet and passes it to the IP software on the client. Seeing that the destination IP address on the packet is its IP address, the client's IP software extracts the data out of the packet and passes it to the TCP software on the client.
The TCP software on the client performs the error check, and if it fails, discards the data.
Meanwhile, the TCP timer on the server times out, so the TCP software on the server retransmits and the whole process is repeated. If the second time, the protocol data unit received by the TCP software on the client passes the error check, it sends an acknowledgement to the server so the server stops retransmitting.
The TCP software on the client extracts the data from the TCP protocol data unit and parks it in a memory space for the application identified by the destination port number on the TCP header... the file transfer application, which picks up the data shortly after.
Meanwhile, the file transfer application on the server is sending the next segment of the file.
Easy as pie.
Related Courses
These topics are covered in online certification courses:- TCO CTA Certified Telecommunications Analyst – Course 2413 IP Networks, IP Addresses, Packets and Routers
- TCO CTA Certified Telecommunications Analyst – Course 2414 MPLS and Carrier Networks
- TCO CTNS Certified Telecommunications Network Specialist – Course 2413 IP Networks, IP Addresses, Packets and Routers
- TCO CTNS Certified Telecommunications Network Specialist – Course 2414 MPLS and Carrier Networks









