In this tutorial, we explain the key ideas underlying what happens when you enter a password to join a Wi-Fi network, authentication, communication security, and how the most popular standard WPA2-Personal works.
A major concern with wireless LANs is security.
Media Access Control (MAC) address filtering is a network security measure that can be implemented: setting the access point to only accept connections from specific wireless LAN interfaces, e.g. a particular laptop.
This protects the network connection from access by unauthorized users – but does not protect legitimate users' transmissions from eavesdropping. If someone can get physically close enough to receive signals, there is no way to prevent them from eavesdropping on communications, which can include intercepting and re-using usernames and passwords and intercepting and "wikileaking" sensitive information.
This is particularly troublesome in coffee shops, airports and anywhere else the communications are not encrypted, "open" hotspots. In 2010, a browser plugin FireSheep was made available that allowed someone sitting in such a coffeeshop to eavesdrop on everyone else's communications – and if a person transmits their username and password in the clear, with one click re-use the username and password to log into that person's account. This means that secure encryption of sensitive communications over the airlink is mandatory.
If it can be ensured that the users always implement client-server encryption (called Transport Layer Security), by using a VPN to connect to work, by always typing https:// for all web surfing, by always using encrypted email and encrypting the data of any other app, then there is no need for encryption of the airlink. Of course, this is unlikely, so encryption of the communications on the airlink, that is, between the access point and the wireless device, must be implemented whenever possible.
This is implemented by entering a password and the generation and sharing of encryption keys. The terminal encrypts its data and the base station decrypts with these keys and vice-versa.
Wired Equivalent Privacy (WEP) was the first encryption algorithm for wireless LANs; but its use is not recommended as there are software tools available that can determine the key in a matter of minutes.
Wi-Fi Protected Access 2 (WPA2) with its AES encryption should be implemented when possible. WPA2 is the Wi-Fi Alliance's name for a security amendment to 802.11 initially referred to as 802.11i then incorporated into the 802.11 standard in 2007.
WPA3 is the latest release, with minor improvements over WPA2.
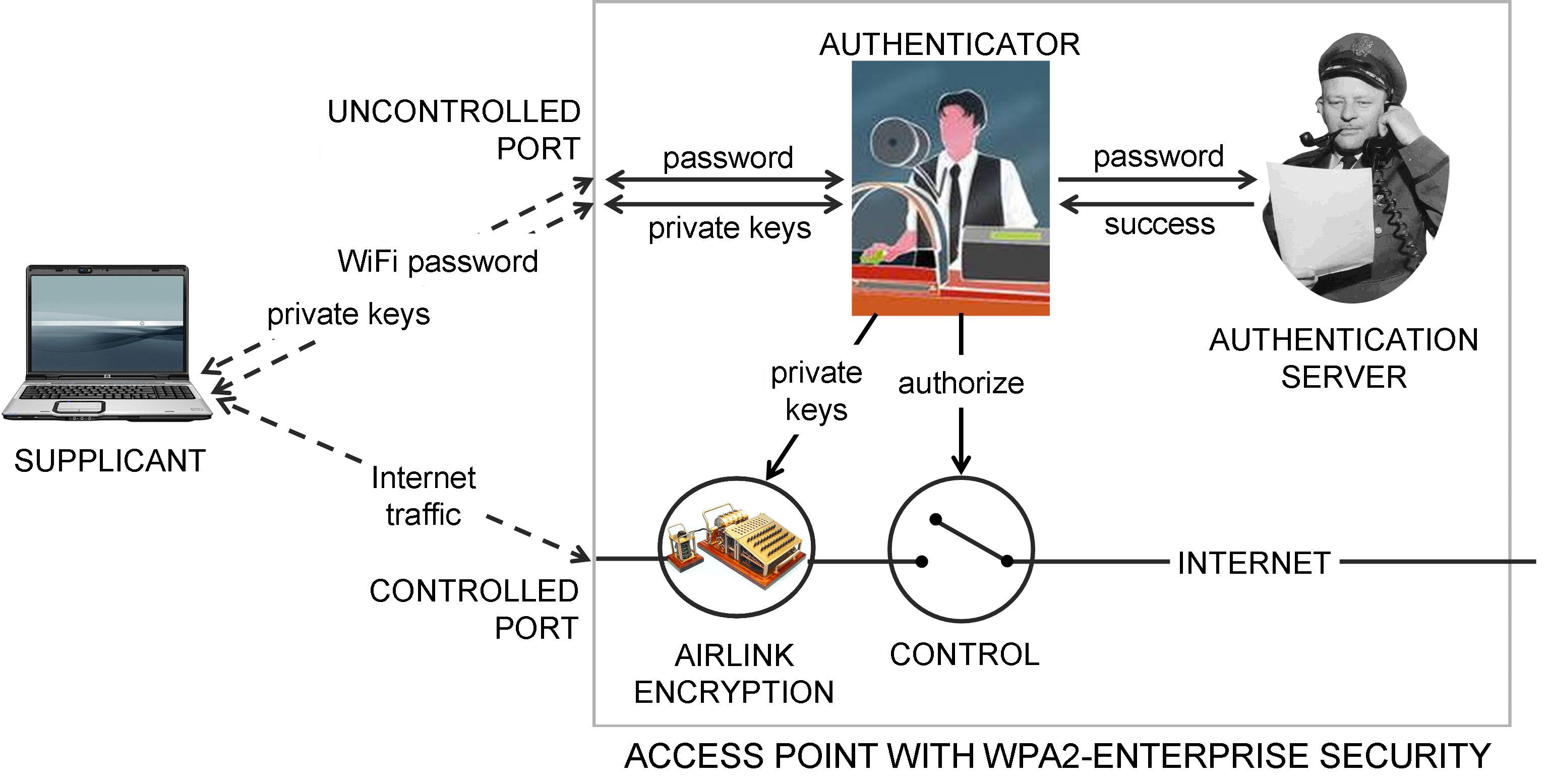
WPA uses a framework called 802.11X Port-based Network Access Control to exchange security messages and block or unblock Internet traffic for a device. 802.11X was initially designed to block or unblock physical hardware ports on LAN switches. For wireless LANs, the term "port" is more of a notion, identifying traffic for a particular device, and the "switch" is the Wi-Fi AP.
Two types of ports are defined on the AP, as illustrated in the diagram above.
One is the Uncontrolled Port, used by all devices to transmit and receive only security messages conforming to the Extensible Authentication Protocol (EAP) for communication of passwords and encryption keys.
The device desiring to communicate is called the supplicant, and the function in the AP it communicates with is called the authenticator. The messages are defined in EAP "methods", including EAP-PWD for passwords and EAP-IKEv2 for key exchange.
The other type of port is the Controlled Port for each device, through which application traffic to other devices flows. In most cases this is traffic to and from the Internet. Sometimes, the other device is locally-attached; for example, the HTTP server front-ending the AP's control panel.
The full implementation, called WPA3-Enterprise, supports multiple users with different passwords. The authenticator communicates with an authentication server using messages conforming to the RADIUS protocol to validate the supplied password, and on success, negotiates a 256-bit private key called the Pairwise Master Key (PMK) with the supplicant.
A simpler implementation, called WPA3-Personal, supports only one password, which either is the 256-bit Pairwise Master Key or a passphrase of 8 to 63 characters that is used to generate the PMK. This is referred to as a Pre-Shared Key (PSK). Since there is only one password, an authentication server is not required. This is implemented in the vast majority of APs.
After successful authentication, private keys for the session are generated and the controlled port is authorized. The PMK and other information is used to generate a private key called the Pairwise Transient Key for bulk encryption of normal ("unicast") traffic between the AP and the device, and a Group Temporal Key for multicast traffic between the AP and multiple attached devices. These keys are exchanged using EAP messages as illustrated.
The controlled port is set to unauthorized when the authentication process begins, meaning that no application traffic is permitted through the AP. After successful authentication and key exchange, the controlled port is authorized, the interrupter-type switch in the diagram closes, allowing Internet and other application traffic through the AP.
This traffic is encrypted on the airlink, that is, between the AP and the device, using strong AES-based encryption.
If you liked this, there are dozens more lessons - including text, graphics and an engaging on-camera instructor in the CWA Certified Wireless Analyst Certification Package. It starts with basic radio principles, covers cellular and mobility from concepts, components and applications to 4G LTE, 5G New Radio, then Wi-Fi, security, satellites and more.









