E-mail was one of the first "killer apps" on the Internet, and has been a major contributor to increases in productivity over the past ten years. Of course, along with email came the scourge of spam. Criminals infect computers with trojan horse programs, creating collections of machines they control remotely to send millions of unsolicited offers for fake watches, pirated software, phony medications and ecard invitations to infect your computer.
As spam reaches 30, 40 or even 100 unwanted messages per day on a targeted account, it is becoming essential to automatically separate legitimate messages from spam. One tool available to senders of legitimate emails to aid the recipient in this process is to digitally sign their messages, allowing the recipient to establish a level of comfort that the message actually came from the indicated sender.
This tutorial originally was sent out as our newsletter by email, which was digitally signed. Your mail client may indicate that it has verified the signature; for example, yahoo mail displays a key icon and gmail states "signed by" below the to: and from: information. This verification can be used to raises the confidence level at your end that the message is legitimate.
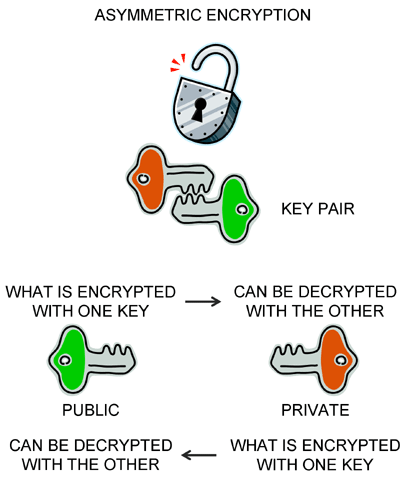
Digital signatures are implemented with asymmetric encryption. Asymmetric means that there are two keys (binary numbers). What is encrypted using one key can be decrypted with the other... and vice-versa. The most popular method of generating key pairs and using them for encryption and decryption was devised by three fellows named Rivest, Shamir and Adelman and is called RSA.
A standard strategy is to generate a key pair, then make one of the keys visible to the public and keep the other key private. Digitally signing a message means the sender using their private key to encrypt selected text and attaching that to the message.
To authenticate the message, that is, verify the digital signature, the recipient can get a copy of the purported sender's public key and use that to try to decrypt the selected text attached to the message. If the decryption using the sender's public key is successful, then the recipient knows that the message was indeed "signed" by the sender (or by someone who stole the sender's private key).
This process is called authentication.
Yahoo developed the Domainkeys strategy, which was standardized as DKIM: Domain Keys Identified Email.
At the sender, a Secure Hash Algorithm (SHA) is used to generate a "hash" or unique binary number representing the email message body and headers such as Message-ID, Received header, the X-Mailer header, Date header, From:, To:, MIME-Version: and Content-Type headers.
This hash is then encrypted with the sender's private key using RSA, and the encrypted hash is added as another message header.
At the receiver, it is necessary to get the sender's public key... so how does the receiver get that? The Domain Name System (DNS) is used. Normally, DNS records relate domain names to IP addresses; but it turns out that the DNS record type TXT that allows free text for comments or domain info was implemented, and this is used to store the domain's public key.
So the receiver examines the domain name of the purported sender, does a DNS lookup to get the DKIM public key for that domain, and uses it to decrypt the hash contained in the email header. The receiver also computes the hash of the received message and compares the two.
If they are not the same, then the message was not sent by that domain (the From: field is false, for example), or the message was altered, and the receiver would generally put the message in the spam folder or garbage where it belongs.
If the hash of the message and the hash in the header are the same, then we have a high confidence that domain sent the message. This knowledge might be combined with other knowledge, for example the reputation of the sending domain, and used to decide the message is "ham" not "spam" and place the message in the inbox.
This sending-domain authentication using digital signatures is one tool in the fight against spam. Teracom has implemented it to help ensure that our newsletter goes into your inbox.
Note that if you want to be absolutely sure these messages go in your inbox, also add "newsletter@teracomtraining.com" to your whitelist / trusted senders / address book... this is the "reputation" part of the previous paragraph.









