This tutorial is from Teracom's Course 150, "Understanding IP Contact Center Technology". Taken from the fourth chapter of the course after a foundation of knowledge is put in place, this is a discussion of one method of monitoring calls in an IP-based contact center.
Analyzing all of the external interactions with customers, suppliers and other third parties is still important. Every business will seek to gain a competitive edge from better understanding their customers and acting on insights contained in interactions with them across all channels. In addition, agent performance, liability concerns and threat management are matters that require some form of call monitoring and recording for all contact centers. But there are issues of how this can be technically accomplished in an IP telephony environment.
Legacy telephone systems had a fairly easy mechanism with which to work. Calls were continuous streams of analog or digital voice, either on the trunk side or the line side of a switch. These streams could be recorded either by physically tapping a circuit or port or copying a TDM channel within the switch. However, voice over IP transmission is performed using independent voice packets representing snippets of a call interspersed with voice packets from other calls, data packets and signaling packets. A physical tap would result in a collection of garbage.
A few vendors have voice over IP recording systems and they use some technical tricks to monitor and record calls. The components involved are call control information translation software, call content recorders, and management and administrative systems. One or more recorders are placed in the contact center network depending upon the size of the network and types of calls that are to be monitored.
The recorders are programmed to monitor or record certain calls; however, the recorders need to know information about the call packets, the Real Time Protocol packets, that would include end-point addressing and type information at a minimum. This signaling level data could come from a CTI server, from direct CTI output from a call control server (this will eventually be replaced by a data application-to-application interface as previously discussed), or it may be gleaned from the call set-up protocol packets, such as SIP packets, as they go by the recorder. Once the proper packets are identified for recording, copies are sniffed or snooped (sucked or plucked if you will) off the network into storage. Markers and labels are added to the recorded content for later identification, retrieval, or analysis by other programs which are part of the recording system.
There are several types of monitoring and recording mechanisms, as a way of classifying the activity. Passive recording means that automated procedures or programmed procedures are in place to record either all of the calls, bulk recording, or certain calls, selective recording, on a link or part of a network. Active recording means a person must initiate the recording process, say an agent who wants to record a threatening or abusive conversation at the moment. In addition to these formal types or recoding there are two other variations to mention. One is the tagging, as it is called, of additional information to the recorded call for use in the analysis phase. Tagged information may include things like the application being used at the time of the call or ANI data of the call. Recording of calls can also be accomplished in the service provider's network as part of a hosted contact center package.
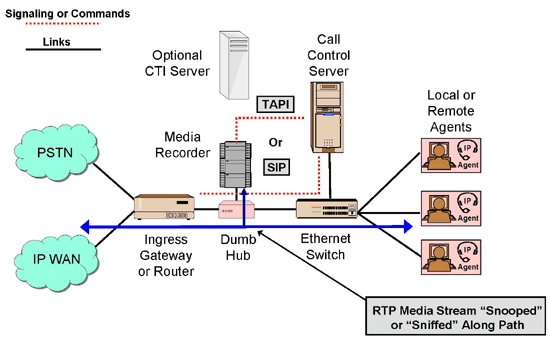
This diagram shows one of the common configurations used to record calls. Incoming and outgoing calls can be recorded by placing the recorder on the trunk side of the IP telephony system. Calls relating to the PSTN will traverse a gateway. Calls relating to an IP WAN will traverse an edge router. The recorder will have access to all external calls sitting logically between the ingress gateway or router and the rest of the telephony system – before the calls are shuttled to other parts of the network. Physically, this may be accomplished by having the recorder connect to the network through a dumb, three-port hub, which broadcasts all packets to all ports including the recorder. The recorder would need a "promiscuous" network interface card to receive all such packets. The recorder is programmed to record all or certain calls whose packets can be identified with CTI information emanating from the call control server or from the call set-up/transfer signaling (SIP for example) going to and from the gateway or router. Remember, the recorder is receiving all traffic through the hub.
The trunk side attached recorder option is a straight forward solution and can capture the external calls at a good aggregation point in the network. This could include self-service and information-gathering calls that go to the IVR before being passed to an agent. This technique is not intrusive and does not consume network bandwidth for the recording process. If CTI information is not available to the recorder, rich information for tagging will not be available. However, internal calls, such as agent to agent, agent to supervisor, etc. will be missed.
Source:Teracom Course 150 "Understanding IP Contact Center Technology", page 4.37
Related Courses
These topics are covered in instructor-led training course:- Course 150 "Understanding IP Contact Center Technology"









